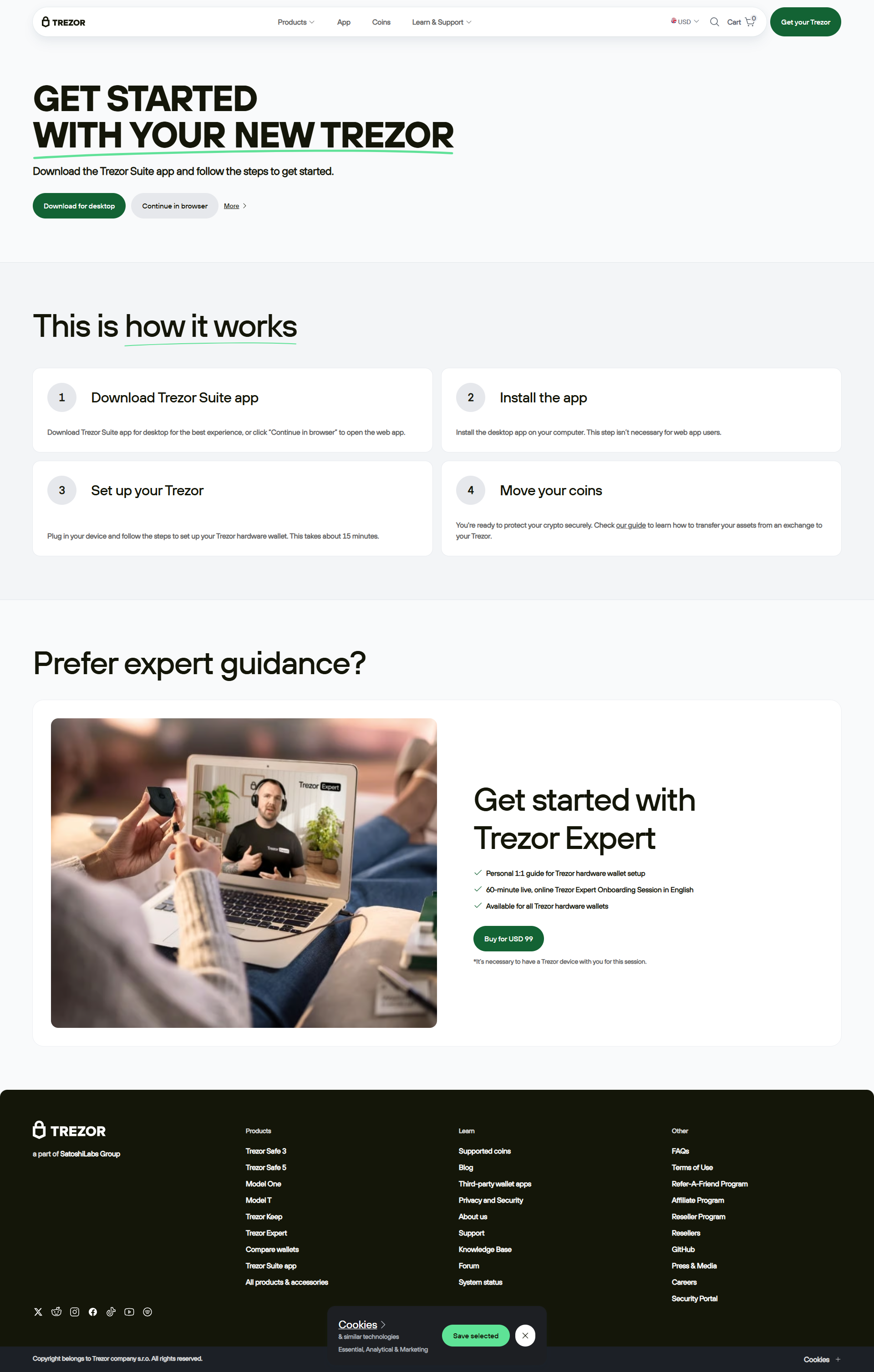
Trezor Login: Your Gateway to Secure Digital Asset Management
Learn how Trezor Login keeps your cryptocurrency safe through advanced hardware encryption, privacy controls, and user-friendly authentication methods.
🔐 What Makes Trezor Login Different?
In a world where phishing links and password leaks dominate headlines, Trezor Login stands apart. It replaces fragile online authentication with a secure, offline hardware confirmation process. Your private keys never leave the device, making unauthorized access virtually impossible.
Unlike centralized exchanges, Trezor’s security model is built around zero trust — even the company itself cannot access your wallet data or funds.
🧩 Understanding How Trezor Login Works
Trezor Login functions through hardware validation. When you attempt to sign in to a supported application or Trezor Suite, your Trezor device signs a unique cryptographic challenge instead of transmitting your password. This prevents online data theft and strengthens identity protection.
- Offline Verification: Your keys are generated and stored only within your Trezor device.
- Randomized PIN Interface: Protects against screen-based or keyboard-based keylogging attacks.
- Button Confirmation: Every login must be physically approved by pressing your device’s button.
- Optional Passphrase: Adds another encryption layer for maximum protection.
⚙️ Step-by-Step Trezor Login Setup
- Download and install Trezor Suite from trezor.io/start.
- Connect your Trezor hardware wallet using the official USB cable.
- Launch Trezor Suite and choose “Access Suite”.
- Enter your device PIN securely using the randomized interface displayed.
- Confirm the login request physically on your Trezor device.
- Access your portfolio and begin managing assets confidently.
💡 Why Hardware Login Beats Online Passwords
Traditional login systems depend on cloud servers and user-generated passwords — both prone to human error and hacker attacks. With Trezor Login, your identity is confirmed through cryptographic signatures generated offline. This ensures that even if your computer or network is infected, attackers cannot impersonate you.
Passwordless Access
Forget remembering passwords. Every login request is verified through your device’s secure chip.
Tamper-Proof Security
Each transaction and login must be approved on the physical device, blocking unauthorized use.
True Ownership
Your private keys never touch the internet, guaranteeing that only you control your assets.
🛠️ Troubleshooting Common Trezor Login Issues
Device Not Found
Reconnect your USB cable or use a different port. Make sure Trezor Bridge is installed correctly.
Incorrect PIN
Wait before reattempting. Remember that repeated incorrect PINs can reset your device for security.
Firmware Error
Download the latest firmware from Trezor Suite to ensure compatibility and fix potential glitches.
📊 Trezor Login vs Traditional Crypto Wallet Access
| Feature | Trezor Login | Traditional Login |
|---|---|---|
| Security Level | Hardware-based encryption | Password protection only |
| Data Exposure | No personal data stored online | Stored on centralized servers |
| Access Method | Physical device approval | Browser or mobile app |
| Vulnerability Risk | Extremely low | High due to online exposure |
💬 Expert Insights
“Hardware logins like Trezor are redefining user authentication — they combine convenience, privacy, and control in ways traditional systems can’t.”
The crypto landscape is shifting toward greater decentralization and personal sovereignty. Trezor Login empowers users to be their own bank, safeguarding funds through self-custody and cryptographic integrity.
🚀 The Future of Crypto Access Starts with Trezor Login
By using Trezor Login, you’re not just signing into your wallet — you’re entering a new era of personal digital security. The blend of hardware encryption, user simplicity, and privacy control makes it one of the safest authentication systems in the crypto world.